[Retibus] — Fil’s Tech Blog
Archived content can be also browsed by tag, series or fuzzy searched.
If you are working on a Webex Calling project, check out the new ⚙️ LGW Config Generator beta!
Businesses that consider hosting their telephony in the cloud often think about survivability as a critical requirement 🔥 It is therefore no surprise that vendors are trying to provide their respective solutions for “survivable” cloud telephony (i.e.: provide service when the cloud is unreachable): I’ve already discussed about Site Survivability for Webex Calling and its architecture (you can check the article here); then there’s Microsoft, which is actively improving their Survivable Branch Appliance (SBA) solution; or Zoom, leveraging their “node” architecture to provide survivable telephony for Zoom Phone....

The Problem There are cases where you need the IOS XE Guestshell to have a separate IPv4 address. A recent example for that is enrolling the router to the Webex cloud as a managed gateway. The Solution In the following steps I will show you how to configure the Azure VM for your virtualized router to make this work. Step 1 - Configure Azure There are many ways you can configure things on Azure, I’m going to show the steps on the web portal....
Introduction If you are reading this, chances are you already know what Let’s Encrypt is about. In this case you can simply skip ahead. Otherwise, in their homepage there is a pretty good description: A nonprofit Certificate Authority providing TLS certificates to 300 million websites. 300 million websites. Wow! Wouldn’t it be nice to use these certificates on your Cisco Routers? Good news! You can. The PKI and the business of buying a certificate Nowadays Public Key Infrastructure (in short PKI) is a fundamental presence behind (all?...
Intro I recently recorded a demo of Webex Calling Site Survivability, in which I was showing in (near) real-time the displays of Cisco IP Phones inside a browser frame. It turns out people liked this little trick, so I’m making it available to the public. In the screenshots below you get the idea of what the end result looks like (the content of the display is the actual content of the physical phone to which the frame is connected to)....

Recently Cisco announced the general availability of a new component in their cloud calling architecture: Site Survivability for Webex Calling Multitenant. I’ve recorded a video demo to show what it looks like. If you want to learn more about the feature, keep reading after the video. Demo The Survivable Telephony Problem If you have been in the IP Telephony business long enough, you are certainly familiar with the concept of SRST (Survivable Remote Site Telephony), which is an incredibly useful piece of the Cisco Unified Communications architecture....

Cisco Webex Calling (Cisco’s cloud PBX offering) enables organizations to quickly deploy an enterprise-grade telephony solution featuring all sorts of device types: hardware phones, soft-phones and video devices. The obvious choice for video devices falls on Webex‒enabled Desk or Room devices. Enrolling these devices on the cloud is as simple as entering a 16 digits code. Once they are provisioned (and fully managed from the cloud), adding PSTN service to them is a matter of one or two clicks at most....
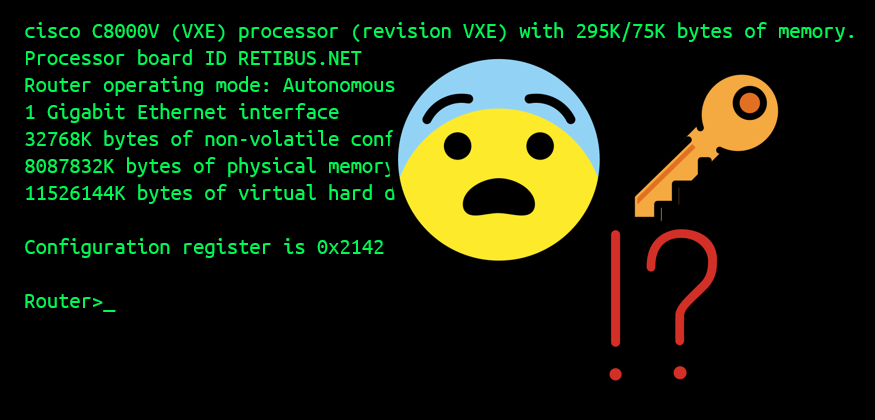
If you lose the password of a Catalyst 8000V or CSR1000V running on Azure, and you would like to perform a password recovery on it, this post might be for you. The Basics of Password Recovery There are useful techniques to authenticate an SSH session on a router without using a password. Yet, there are cases where we might have to use password authentication nonetheless. If the password is lost, the next step would be entering ROMmon and perform the usual configuration register change....
When commissioning a new router, you can setup your user for password-less SSH authentication. The only info you need is your public SSH key. The general server side configuration in IOS-XE is all described in the Secure Shell Configuration Guide, and there are very useful security guidelines described in this community blog post (make sure your key complies with the hardened algorithm selection though). Note: I use ECDSA keys because they are shorter, and the IOS-XE CLI appears to better “digest” them ¯\_(ツ)_/¯...